Overview
In this tutorial you'll learn the best practices for building authorization enforcement into your applications. We recommend an iterative approach to development that uses the steps outlined below.
| 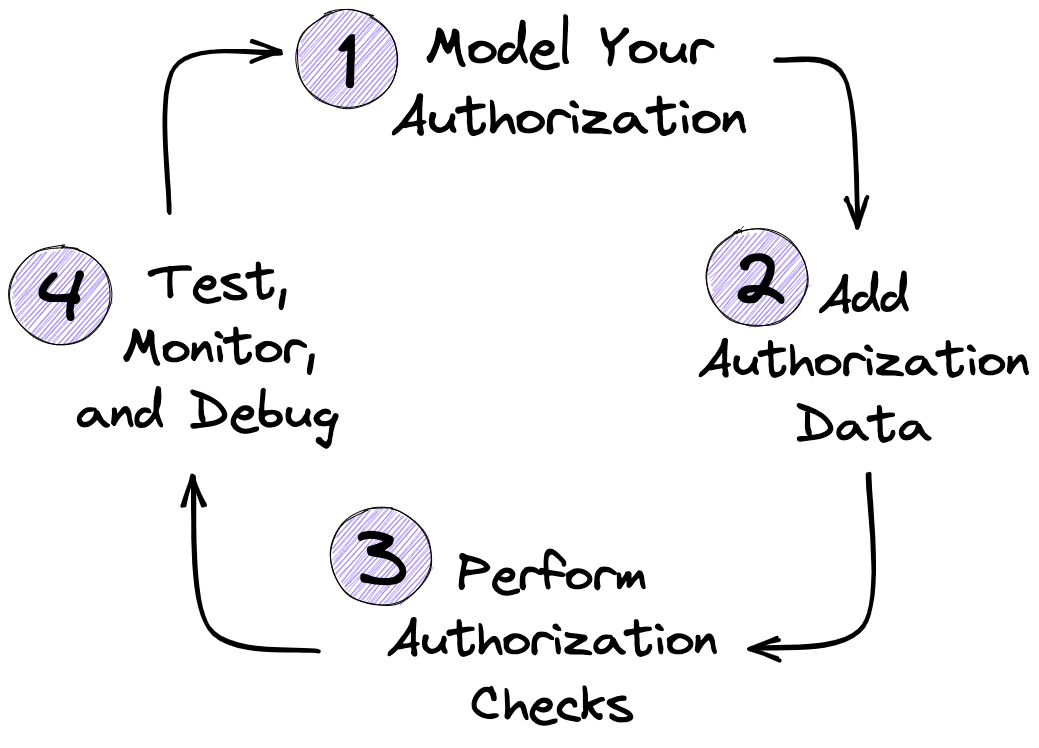 |
In the following section you'll learn about the authorization patterns you can use to model your application. When are ready to implement a particular pattern, go through each step before adding new patterns to your policy.
Talk to an Oso Engineer
If you'd like to learn more about using Oso Cloud in your app or have any questions about this guide, connect with us on Slack. We're happy to help.